Software Composition Analysis
End of Life Notice: SCA / Source Repositories will be removed from Bytesafe
As part of our commitment to keeping pace with the evolving cybersecurity landscape, we are announcing the discontinuation of the Source Repositories feature in Bytesafe, effective July 31, 2024.
This strategic shift allows us to better align with industry standards and enhance our security and compliance capabilities through SBOM Observer.
Software composition analysis (SCA) identifies what open source dependencies are used in a registry, source repository or for a specific component.
Common use cases for Software Composition Analysis include detecting security vulnerabilities, license compliance issues and to produce Software Bill of Materials, SBOM, a standardized and shareable list of components in a piece of software.
SCA components of Bytesafe:
- Source repositories - Git repositories linked to Bytesafe or imported from an SBOM. The Source Repository Scanner detects components in repositories and uses project files to identify both direct and transitive dependencies (software assets).
- Issues - Track security and license compliance for linked source repositories and for any package version held in an active Npm, Maven or NuGet registry. Search for specific packages, vulnerabilities, CVEs and review activity logs.
- SBOM - Export standardized lists of the components and dependencies in linked source repositories.
SBOM Observer - Complete SBOM Solution for DevSecOps
Looking for a solution specialized in managing Software Bill of Materials (SBOMs) at scale?
Discover SBOM Observer, our advanced platform designed for the efficient management, enrichment, and sharing of SBOMs. Supporting over 25 ecosystems and key standards like CycloneDX, SPDX, SLSA, and VEX, it ensures compliance and security for modern enterprises. Enhance your DevSecOps with SBOM Observer.
Learn more at the SBOM Observer Product Site.
Supported Ecosystems
Bytesafe supports a growing number of ecosystems and package managers. Use the table below to set up your repository for the most accurate results.
| Ecosystem | Package Manager | Level (?) | Files | Comment |
|---|---|---|---|---|
| Javascript | npm | DIRECT | package.json |
|
| Javascript | npm | EXACT | package-lock.json |
both v1 and v2 lock-files are supported |
| Javascript | yarn | EXACT | yarn.lock |
|
| Javascript | pnpm | EXACT | pnpm-lock.lock |
|
| .Net | nuget | DIRECT | *.csproj *.vbproj *.fsproj |
projects using <PackageReference/> specifiers |
| .Net | nuget | EXACT | packages.lock.json |
see <RestorePackagesWithLockFile> |
| .Net | nuget | DIRECT | packages.config |
projects using legacy file to specify dependencies |
| Java | gradle | EXACT | build.gradle (or build.gradle.kt) gradle.lockfile |
|
| Java | maven | NONE | pom.xml |
currently unsupported |
| Python | pip | EXACT | requirements.txt |
virtualenv based projects pip freeze > requirements.txt) |
| Python | poetry | EXACT | pyproject.toml poetry.lock |
https://python-poetry.org/ |
| Python | pipenv | EXACT | Pipfile.lock |
https://pipenv.pypa.io/en/stable/ |
| Go | go | EXACT | go.mod go.sum |
Analysis levels
Bytesafe provides different levels of accuracy depending on the ecosystem and available files in the repository. For the most accurate results, generate the appropriate lock-files and commit them to the repository.
| Level | Description |
|---|---|
| EXACT | Most accurate analysis which includes both direct and transient dependencies with exact versions. |
| BEST EFFORT | Dependencies are resolved natively by Bytesafe. In some cases this can deviate in what version is resolved compared to what the ecosystem build tools would. Only direct dependencies are identified. |
| DIRECT | Only direct dependencies are identified. |
| NONE | No dependencies are identified. Add the appropriate project-, and lock-file to the repository for analysis. |
Source repositories
Bytesafe allows users to add Git repositories as well as SBOMs for continuous dependency and weakness analysis.
Most projects use open source dependencies. The direct dependencies are listed in project files like package.json (npm), pom.xml (Maven) or .csproj (NuGet).
Direct dependencies often have dependencies of their own - transitive dependencies, which makes the total number of dependencies much larger.
The Source Repository Scanner detects components in your repositories and uses existing lock files and project files to identify both direct and transitive dependencies.
Add a source repository (Git)
New source repositories can be added using either the URL of a Git repository or selected directly from a list of linked GitHub repositories when using the GitHub integration.
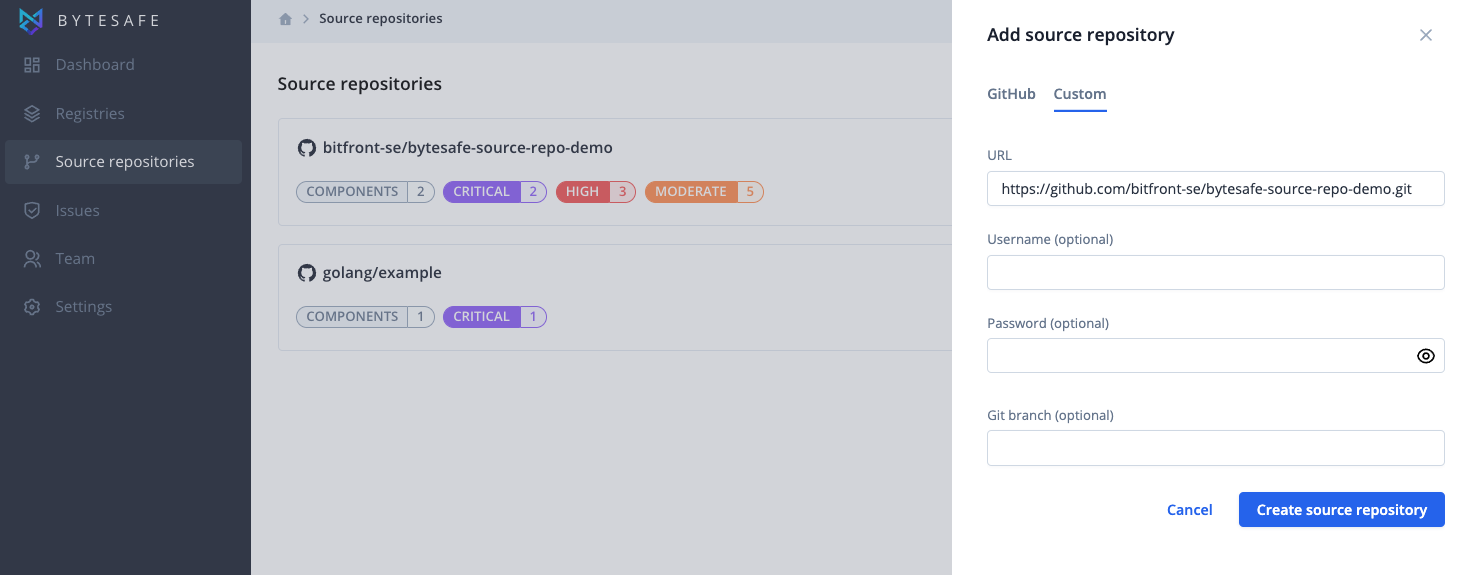
If the Git repository you are adding is private, provide credentials in the form.
Git branch information is optional. If none is provided the default branch will be selected.
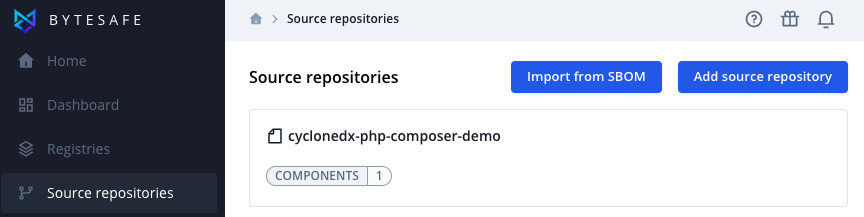
Import SBOM
New source repositories can be added using a CycloneDX formatted JSON SBOM by clicking on the Import SBOM in the web interface:
To use in existing CI/CD workflows, an SBOM can also be imported using the following API call:
$ cat sbom.json | curl -d@- \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer <TOKEN>' https://<WORKSPACE>.bytesafe.dev/import/sbom
The /import/sbom API endpoint takes the following parameters
| Parameter | Description |
|---|---|
| name | Overides the detected name in to SBOM |
After adding a source repository, users are presented with a list of detected components. Select a component or view issues, the log and history in the available tabs on the page.
| Tab | Description |
|---|---|
| Components | List of components found by the scanner. Based on identified project files, e.g. package.json for an npm project. |
| Issues | Lists issues filtered for the source repository (all components) |
| Log | Log for the latest snapshot created. |
| History | List the snapshot history for the source repository together with the Git commit for that snapshot. Select a snapshot from history to see details. |
| Settings | Settings for the source repository. Edit the repository URL or delete the source repository from Bytesafe. |
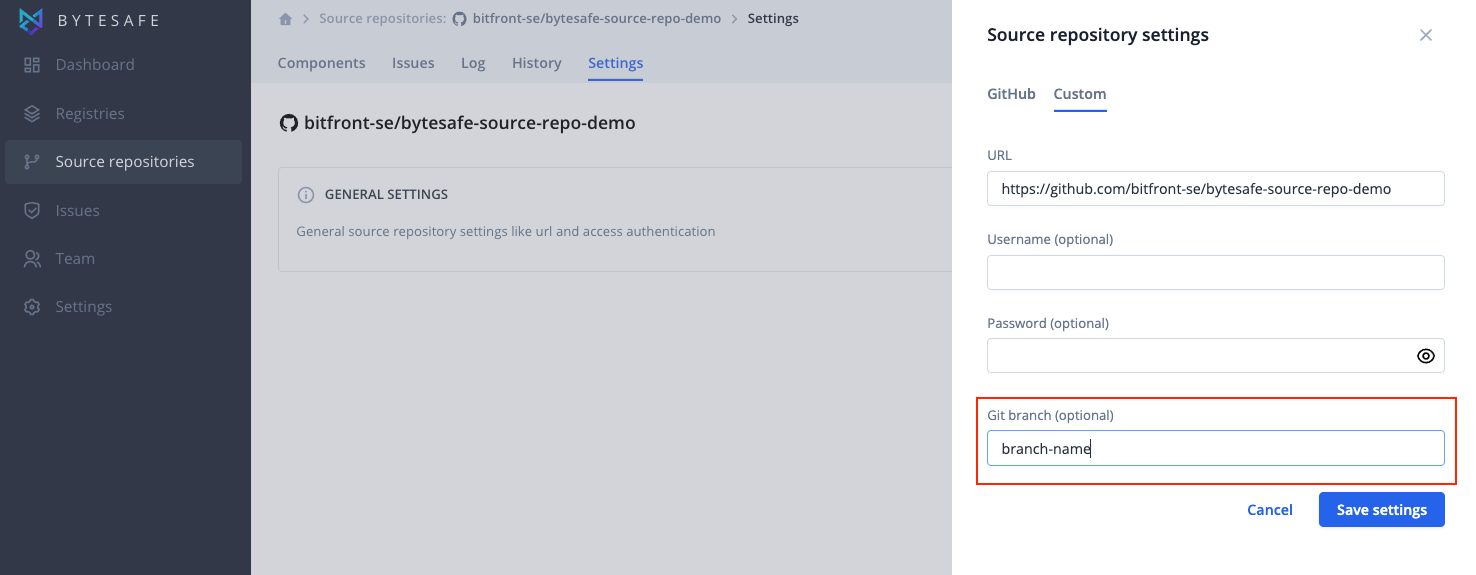
Select Git branch
If no other information is provided Bytesafe selects the default Git branch when adding a Git repository.
To select another branch, enter the branch name either when adding a new Source repository or edit the settings of a current one on the Settings tab.
Scan frequency
Source repositories are scanned every 24 hours, starting from the point in time when a source repository was added. In addition, repositories are scanned vulnerabilities are added or updated in our database.
Additionally, users can enable rescan automation by adding the GitHub integration. Whenever project or lockfile changes are detected in a commit, Bytesafe will automatically scan the repository and create a new snapshot.
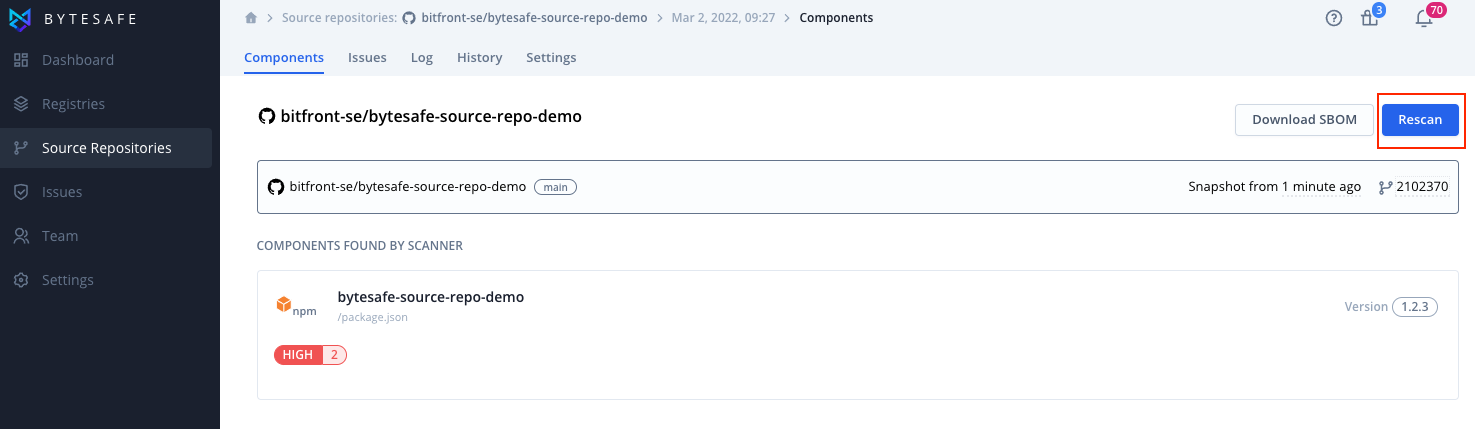
Trigger scan manually
In addition to scheduled and automated scans on changes, users can trigger scans manually in Bytesafe.
On any source repository page, click the Rescan button to create a new snapshot.
Detected components
The source repository scanner will detect components in folders up to three levels deep from the root of the project.
Multilanguage monorepos are supported, so multiple components of different types can be detected in the same repository.
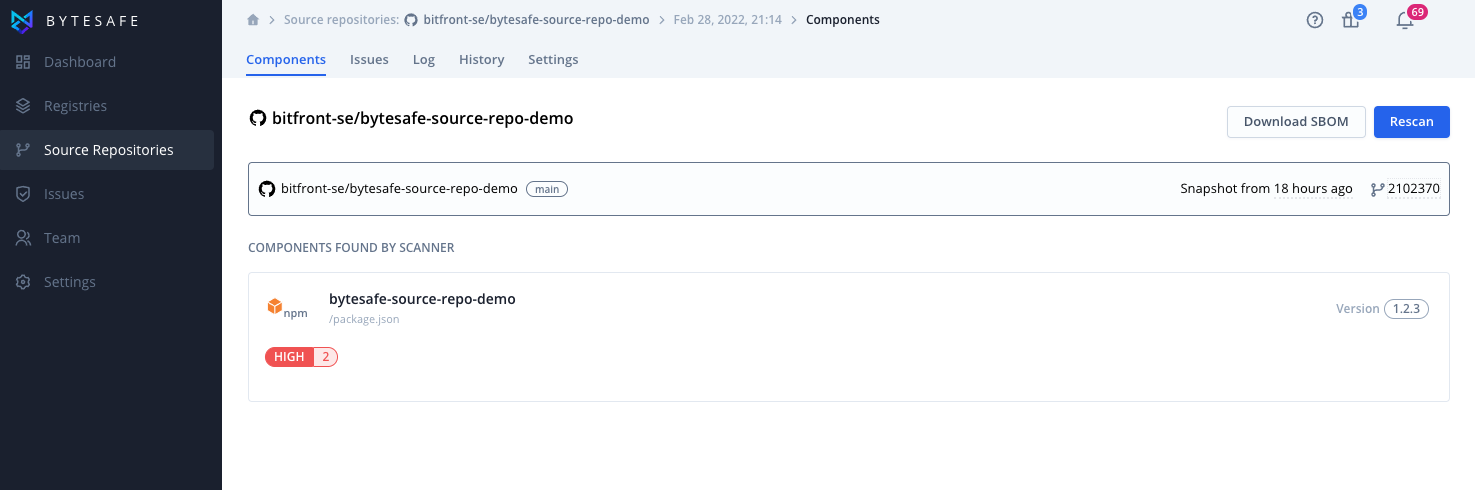
Components and their types are identified based on identified project files, e.g. package.json for a npm project.
Select a component to view the detected dependencies, download SBOMs, review issues, read the log and see previous snapshot history.
Issues
Issues are automatically created when vulnerabilities are found for dependencies identified by the source repository scanner.
Issues can be searched and filtered on status, type and severity. For general information see Issues.
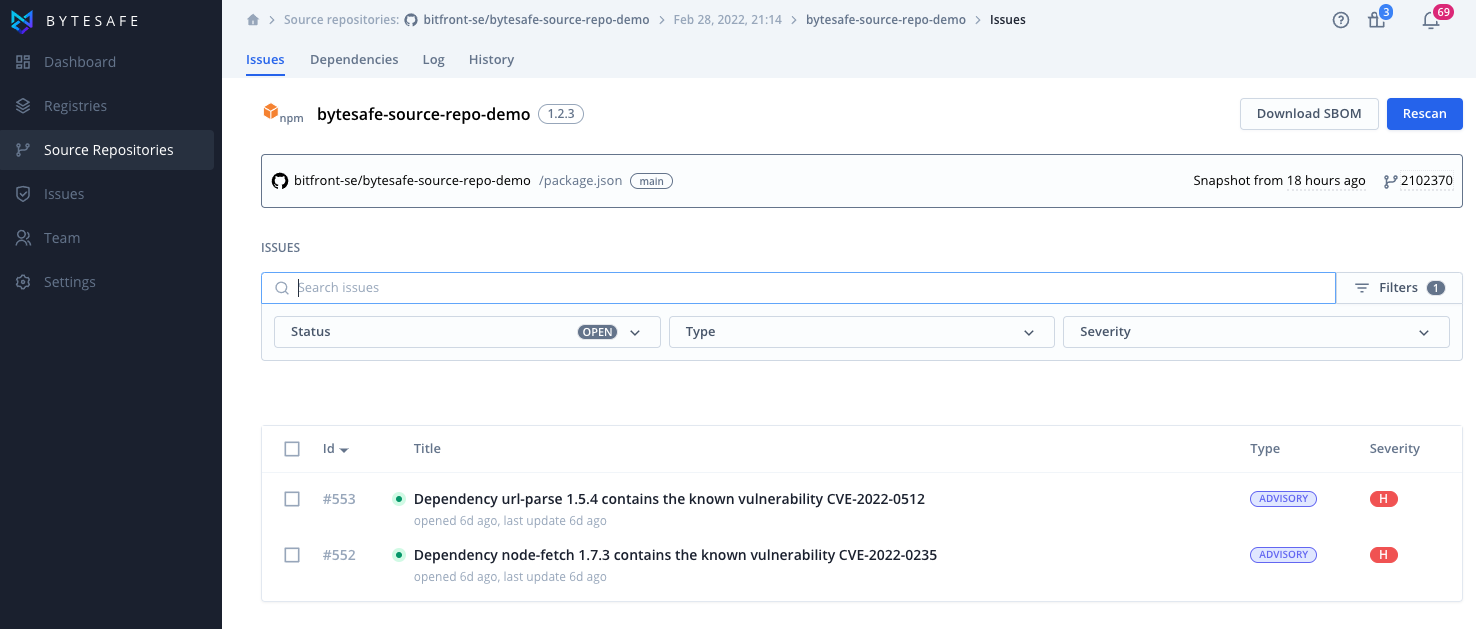
Users will automatically be notified of any found issues.
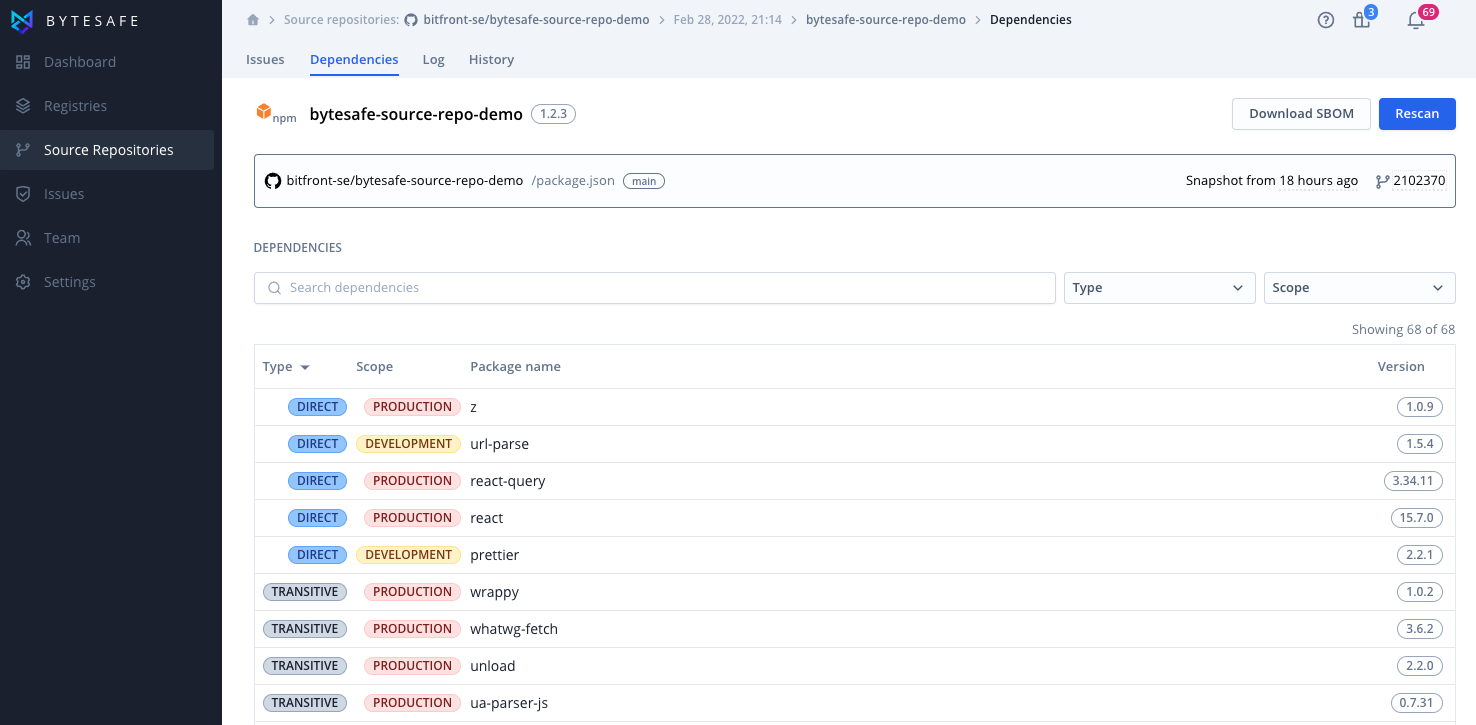
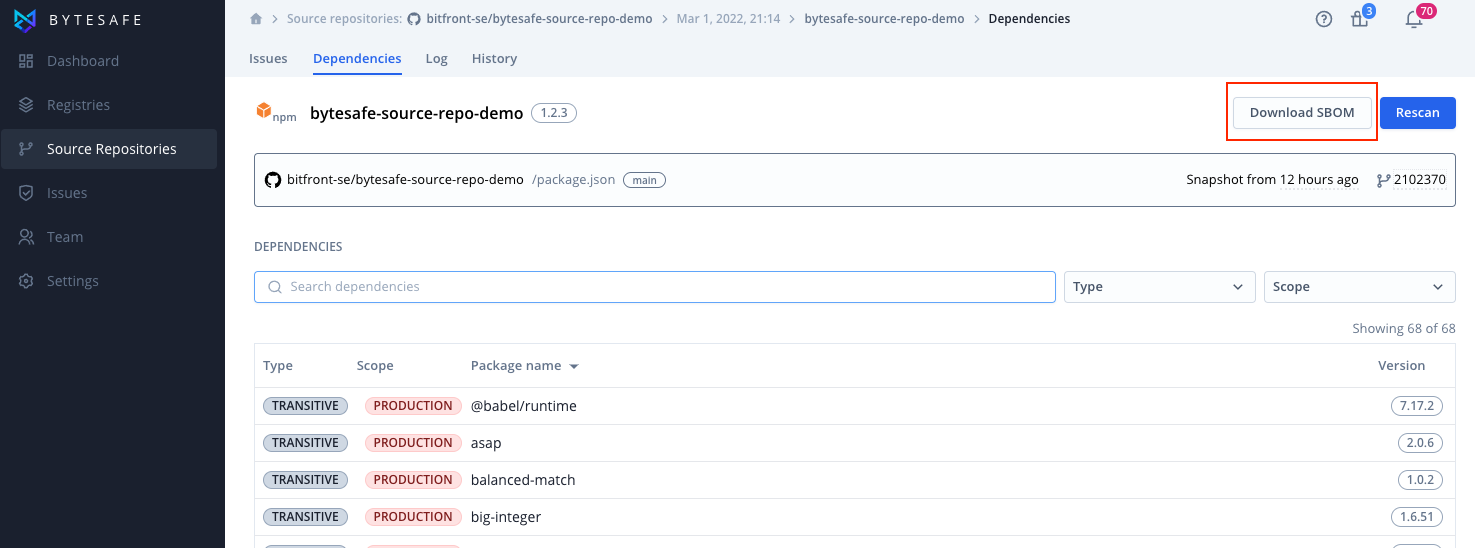
Dependencies
The source repository scanner analyzes lock files and project files to identify the exact dependencies and versions used for a component at a specific time.
Dependencies found will be displayed in the Dependencies list.
The list includes the package name and version, but also information on the type (direct or transitive dependency) as well as the scope (production, development, or test).
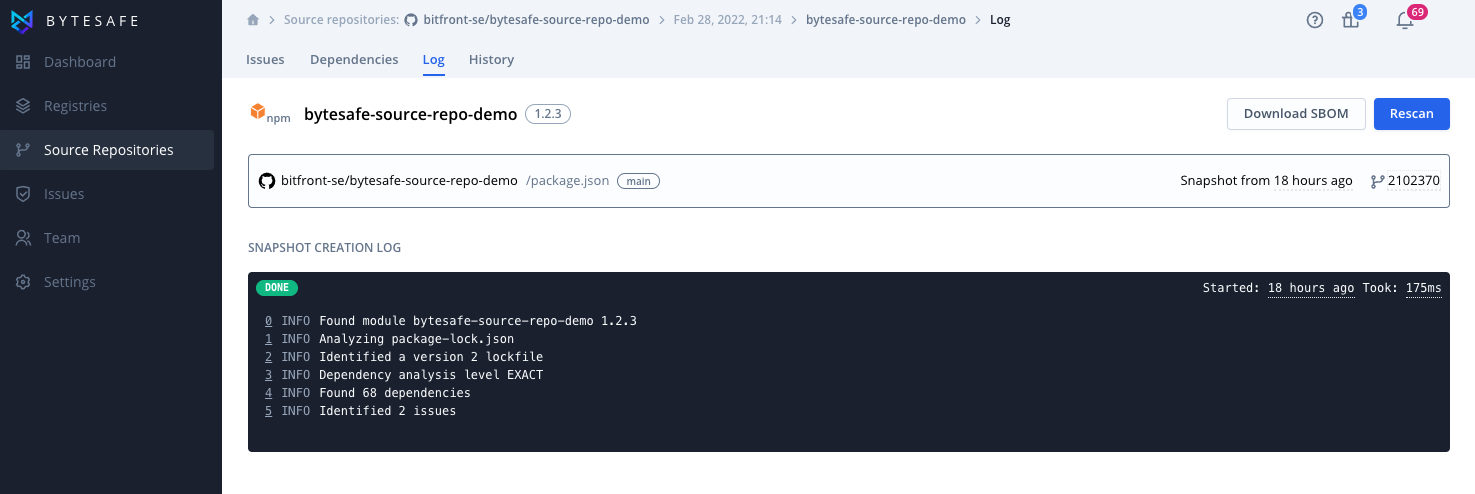
Log
The snapshot creation log details information relating to the creation of a snapshot. This includes information on the number of dependencies, issues and source files.
The log can also be used to troubleshoot failed or missing snapshots, missing components etc.
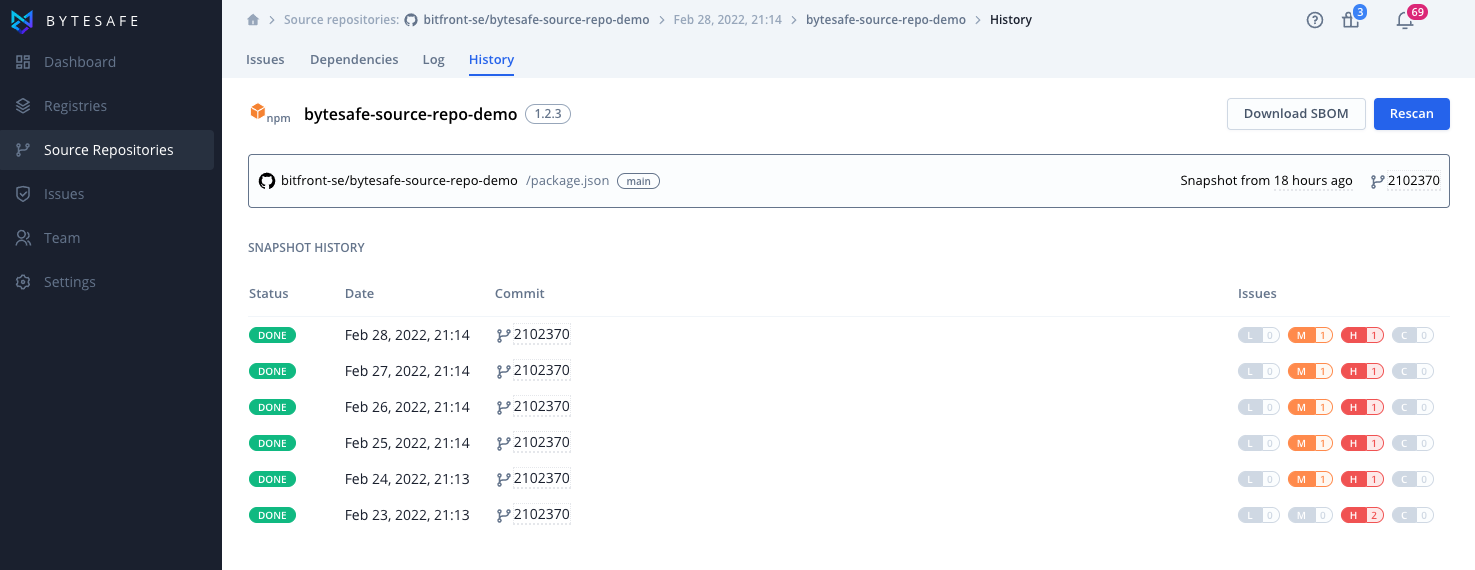
History
Source repositories are periodically scanned according to the scan frequency. Each scan creates a snapshot that contains the state of the source repository at a specific time and commit. The history tab allows users to view their history of snapshots and easily switch between them.
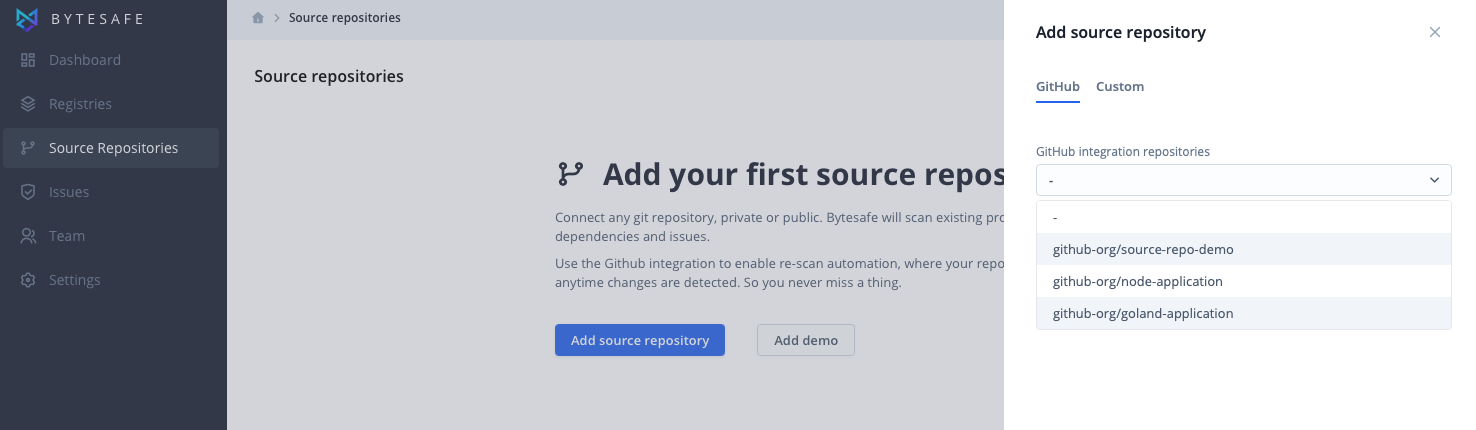
Integration with GitHub
With an active GitHub integration source repository analysis in Bytesafe can be added for any linked GitHub repository.
Select the GitHub tab when adding a new source repository, open the drop down list and select a repository.
Rescan automation when detecting changes
A main benefit of the GitHub integration is that source repositories and components will automatically be rescanned when changes are detected in project files in the repository.
When a new commit alters the package dependencies in the GitHub repository, the integration automatically notifies Bytesafe.
Software Bill of Materials (SBOM)
Software Bill of Materials (SBOM) are standardized and shareable lists of the components in a piece of software.
SBOMs in Bytesafe are JSON files in a CycloneDX format.
# Example: SBOM JSON file for the Bytesafe source repo demo component
{
"bomFormat": "CycloneDX",
"specVersion": "1.4",
"serialNumber": "urn:uuid:ceafb7f8-996e-11ec-96f6-0213bb11c0fe",
"version": 1,
"metadata": {
"timestamp": "2022-02-28T20:14:17Z",
"tools": [
{
"vendor": "Bytesafe",
"name": "Bytesafe SBOM generator",
"version": "1.0.0"
}
],
"component": {
"bom-ref": "pkg:npm/bitfront-se/bytesafe-source-repo-demo@1.2.3?repository_url=https:/github.com/bitfront-se/bytesafe-source-repo-demo",
"type": "library",
"name": "bytesafe-source-repo-demo",
"version": "1.2.3",
"purl": "pkg:npm/bitfront-se/bytesafe-source-repo-demo@1.2.3?repository_url=https:/github.com/bitfront-se/bytesafe-source-repo-demo"
}
},
"components": [
{
"bom-ref": "pkg:npm/%40babel/runtime@7.17.2",
"type": "library",
"group": "@babel",
"name": "runtime",
"version": "7.17.2",
...
SBOMs can be downloaded either for a specific component or for all the components found in a source repository.
To export an SBOM, click the Download SBOM button on the applicable page.
For more information on the CycloneDX format, visit CycloneDX.org.
Integration with Trivy and Github Actions
Using Trivy and Github Actions to keep track of your application’s dependencies and potential vulnerabilities is easy and quick to set up. By using the two extra steps in your build pipeline you get notified when new vulnerabilities are discovered and issues are automatically closed when fixed, without need to track and update issues manually.
- name: Run Trivy vulnerability scanner in fs mode
uses: aquasecurity/trivy-action@0.11.0
with:
scan-type: 'fs'
scan-ref: '.'
format: 'cyclonedx'
exit-code: '1'
output: trivy-sbom.json
Once the CycloneDX formatted SBOM is created above, next step sends it to your Bytesafe workspace.
- name: Upload SBOM to Bytesafe
env:
BYTESAFE_TOKEN: ${{ secrets.BYTESAFE_TOKEN }}
BYTESAFE_ENDPOINT: https://<workspace>.bytesafe.dev/import/sbom
run: |
curl --fail -d@trivy-sbom.json -H 'Content-Type: application/json' \
-H "Authorization: Bearer $BYTESAFE_TOKEN" \
$BYTESAFE_ENDPOINT?name=MyApplication
Note We use the parameter name in the API call above to override the name in the SBOM (which in the above case would just have been .)
SBOM Observer - Complete SBOM Solution for DevSecOps
Looking for a solution specialized in managing Software Bill of Materials (SBOMs) at scale?
Discover SBOM Observer, our advanced platform designed for the efficient management, enrichment, and sharing of SBOMs.
Supporting over 25 ecosystems and key standards like CycloneDX, SPDX, SLSA, and VEX, it ensures compliance and security for modern enterprises. Enhance your DevSecOps with SBOM Observer.
Learn more at the SBOM Observer Product Site.