Role-based access control
User roles allow you to assign special privileges that specify what a user can see and do within your Bytesafe workspace.
These roles help you categorize your users into teams, and assign them different capabilities so that they can do what they need to do without getting in each other’s way.
They’re especially useful for larger organizations, with multiple teams, where there are different groups of employees responsible for different areas (i.e. SecOps team manages dependency firewalls).
Built-in user roles
Bytesafe have a number of built-in roles that manages permissions for common tasks. The initial user that creates the workspace is automatically assigned the
| Role | Description |
|---|---|
| Account owners can update account settings, manage users and close the account. | |
| admin | Admins can invite and manage users, including their roles, |
| billing | Billing managers can access and update billing information, |
| developer | Developers can manage packages, registries, repositories and their associated settings. All new users are assigned this role. |
| Read-only users are ideal for keeping colleagues and stakeholders up to speed when you don’t require the whole range of Bytesafe features, such as uploading and downloading packages. Read-only users do not need a paid seat in the subscription plan. |
Managing user roles
You can change the roles assigned to a user from the Teams menu.
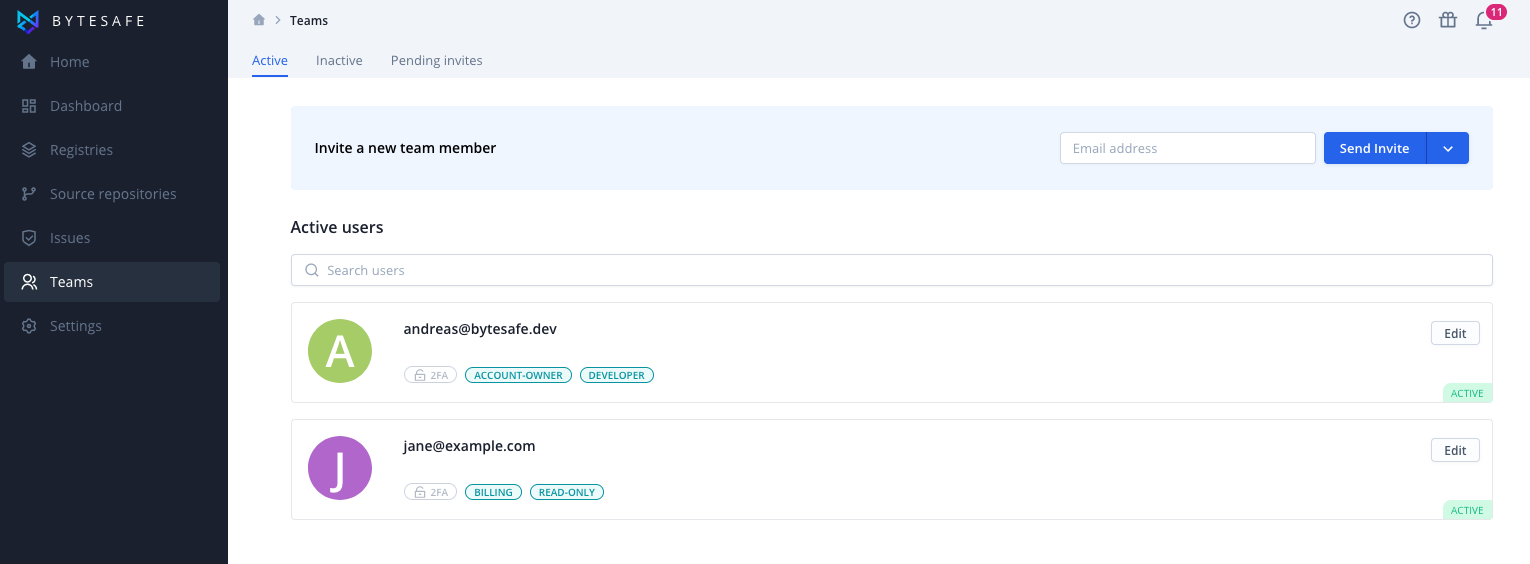
Klick the Edit button to open the sidepanel with user settings.
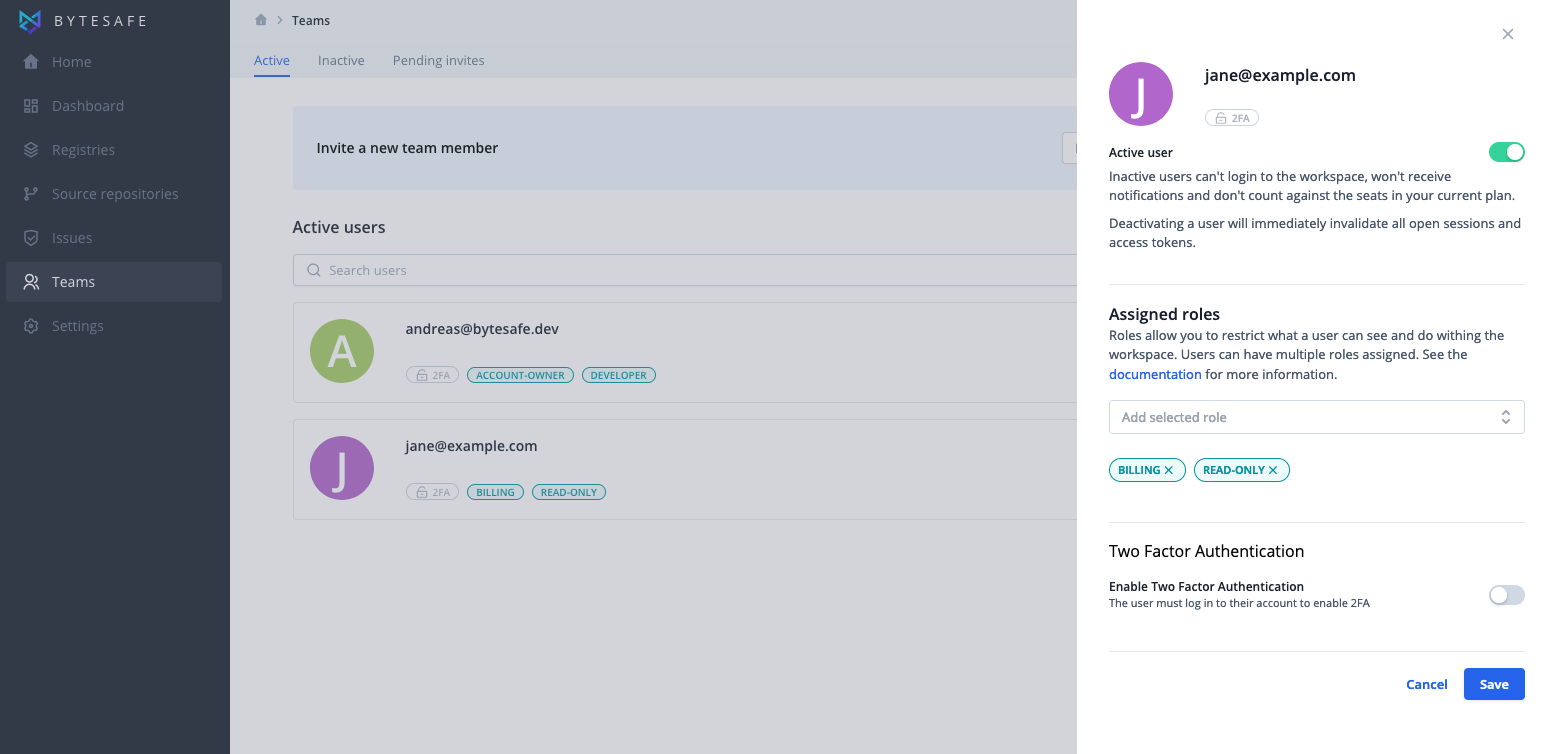
Users must have at least one role assigned.
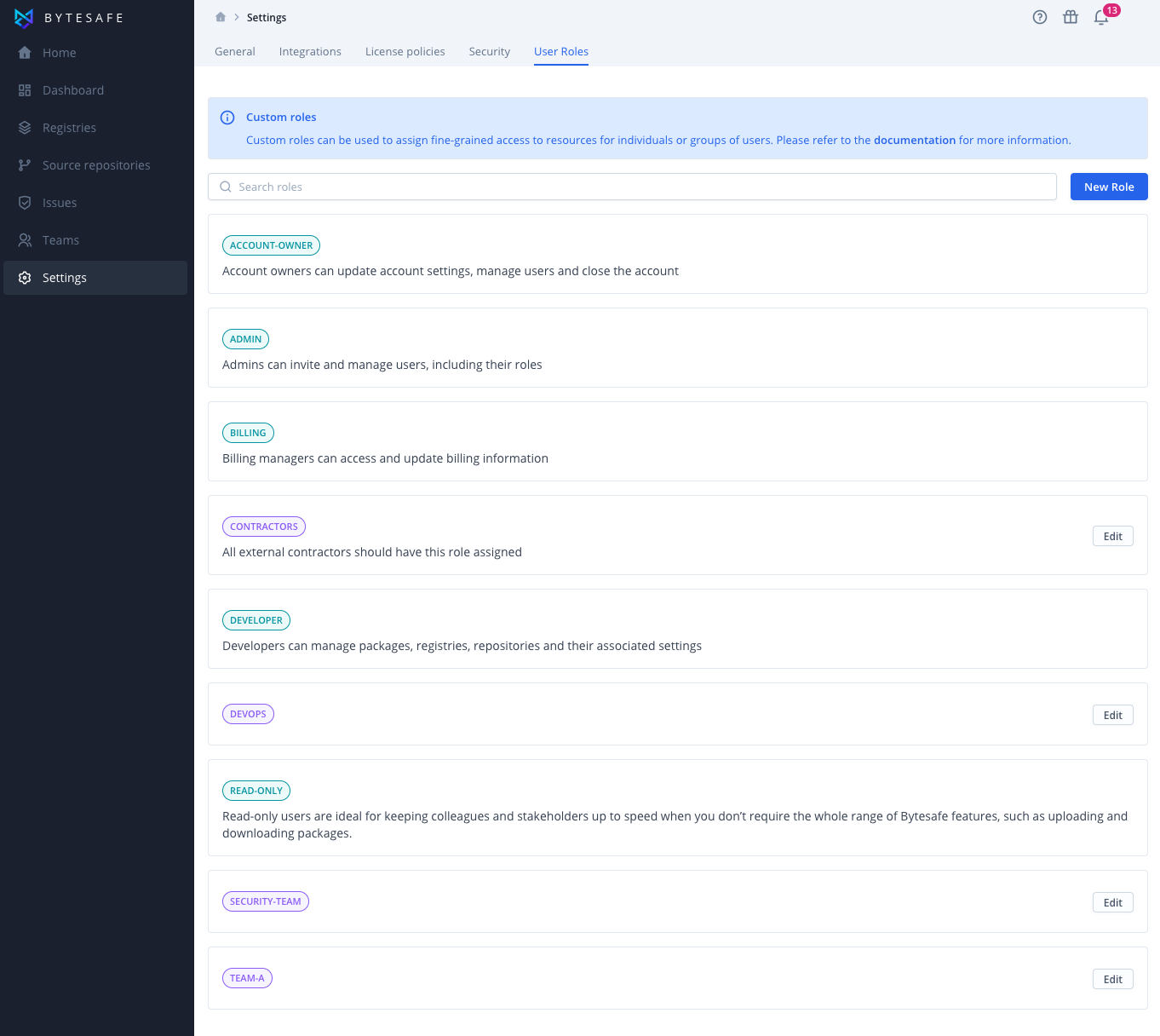
Custom user roles
I addition to the built-in roles, you can create custom roles to manage access to firewalls, registries and source repositories. You can use there roles to group users by teams, or function. Enterprise users can map their existing directory user groups as part the the onboarding process.
You can manage custom roles from the account settings, User roles.
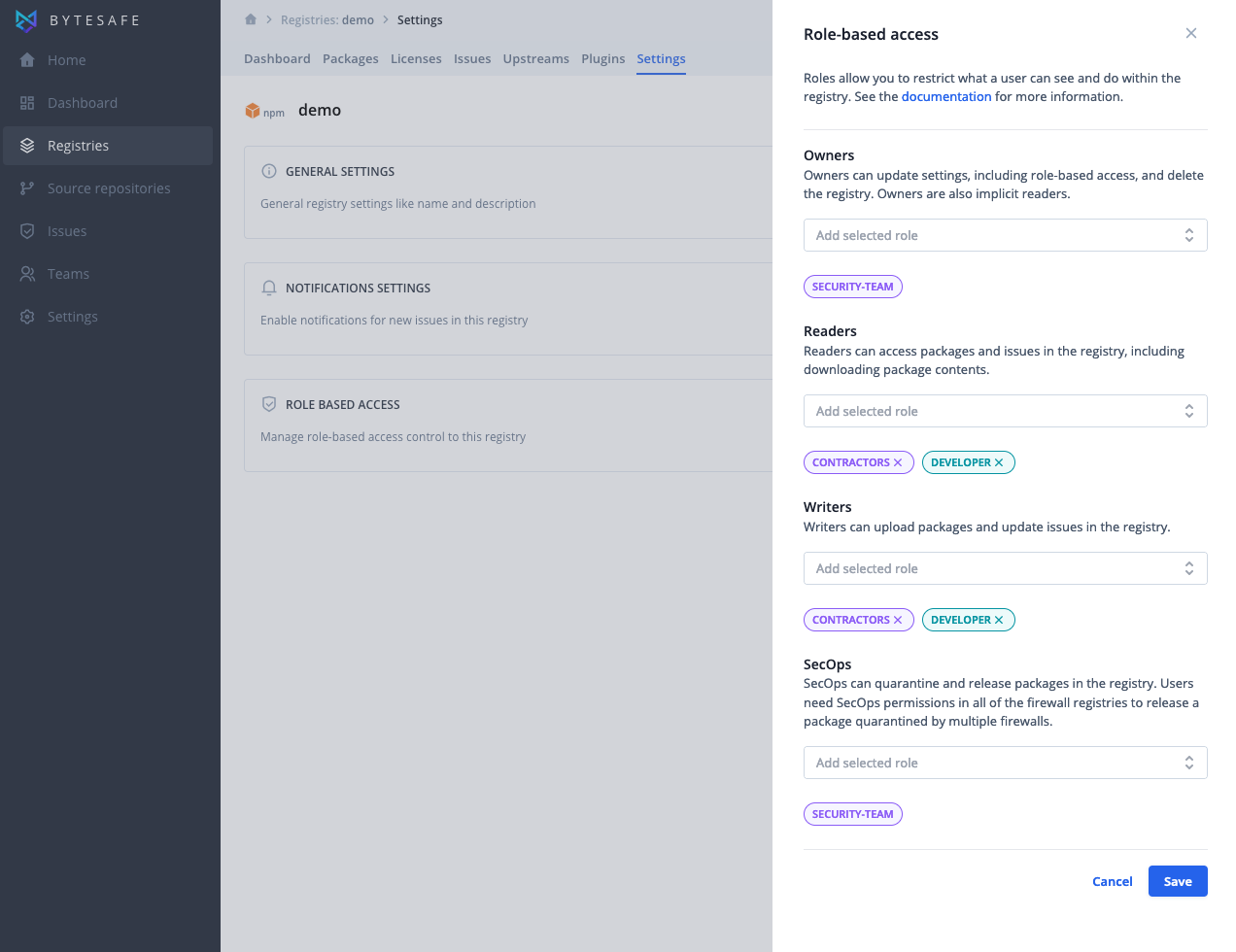
Managing registry access
The different actions a user can perform on a registry are governed by sets of permissions. These sets of permissions can be assigned to one or more user roles.
| Description | |
|---|---|
| Owners | Owners can update settings, including role-based access, and delete the registry. Owners are also implicit readers. |
| Readers | Readers can access packages and issues in the registry, including downloading package contents. |
| Writers | Writers can upload packages and update issues in the registry. |
| SecOps | SecOps can quarantine and release packages in the registry. Users need SecOps permissions in all of the firewall registries to release a package quarantined by multiple firewalls. |
Registry access for read-only users
To assign permissions to user roles, open the registry settings for Role-based access:
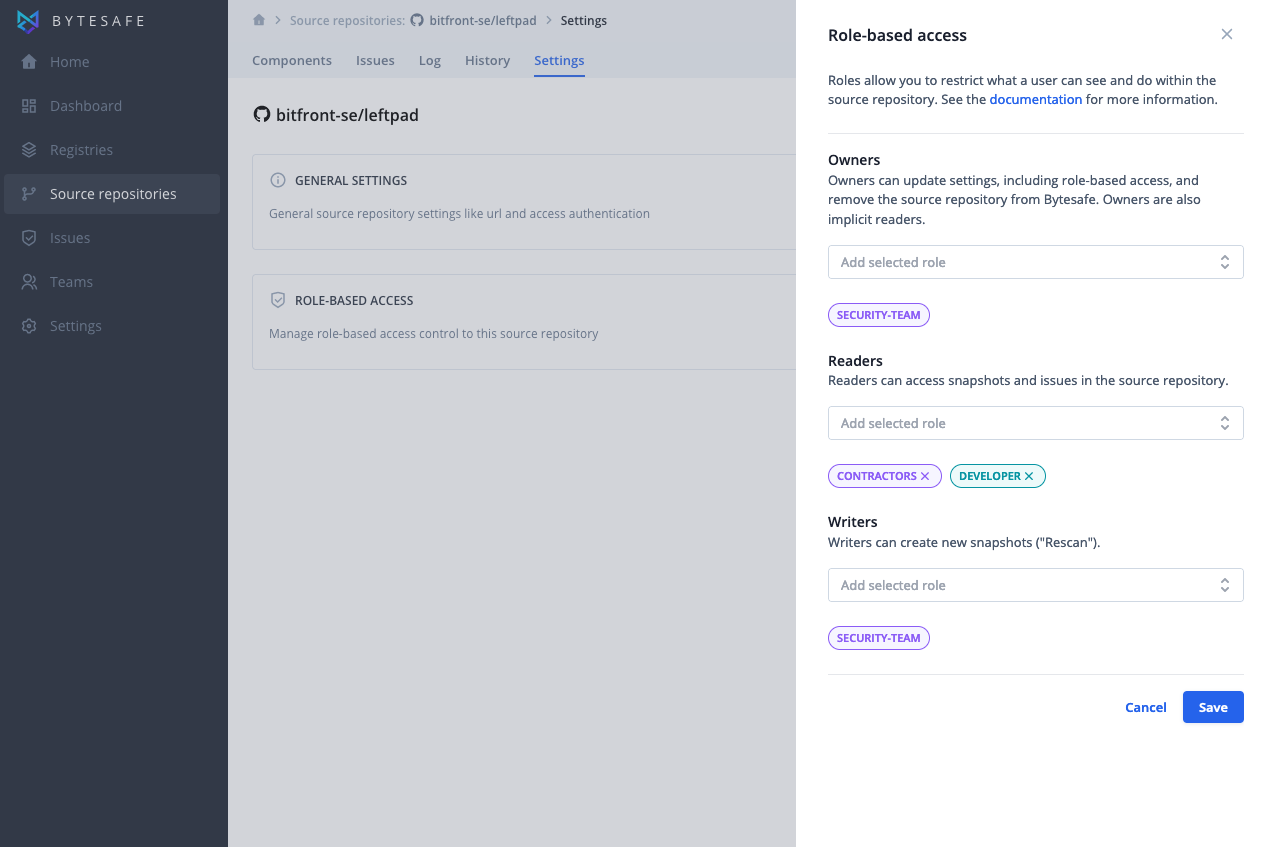
Managing source repository access
The same as for registries, the different actions a user can perform on a source repository are governed by sets of permissions. These sets of permissions can be assigned to one or more user roles.
| Description | |
|---|---|
| Owners | Owners can update settings, including role-based access, and remove the source repository from Bytesafe. Owners are also implicit readers. |
| Readers | Readers can access snapshots and issues in the source repository. |
| Writers | >Writers can create new snapshots ("Rescan"). |
To assign permissions to user roles, open the source repository settings for Role-based access:
Managing user status
Users can be deactivated if they leave your organisation. When a user is deactivated, all access tokens for that user are automatically expired. There is no need to remove individual roles to revoke access to the workspace.